300-215 Online Practice Questions and Answers
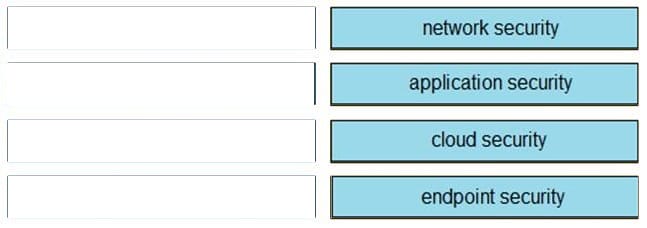
DRAG DROP
Drag and drop the steps from the left into the order to perform forensics analysis of infrastructure networks on the right.
Select and Place:
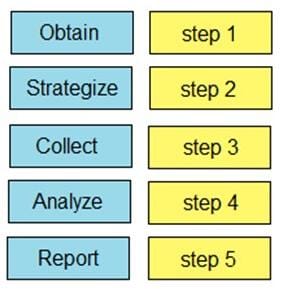
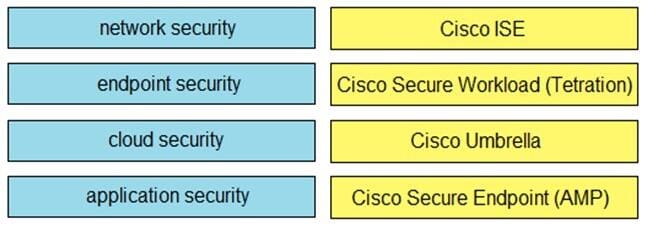
DRAG DROP
Drag and drop the capabilities on the left onto the Cisco security solutions on the right.
Select and Place:
An engineer is investigating a ticket from the accounting department in which a user discovered an unexpected application on their workstation. Several alerts are seen from the intrusion detection system of unknown outgoing internet traffic from this workstation. The engineer also notices a degraded processing capability, which complicates the analysis process. Which two actions should the engineer take? (Choose two.)
A. Restore to a system recovery point.
B. Replace the faulty CPU.
C. Disconnect from the network.
D. Format the workstation drives.
E. Take an image of the workstation.
Which scripts will search a log file for the IP address of 192.168.100.100 and create an output file named parsed_host.log while printing results to the console?

A. Option A
B. Option B
C. Option C
D. Option D
What is the steganography anti-forensics technique?
A. hiding a section of a malicious file in unused areas of a file
B. changing the file header of a malicious file to another file type
C. sending malicious files over a public network by encapsulation
D. concealing malicious files in ordinary or unsuspecting places
A security team detected an above-average amount of inbound tcp/135 connection attempts from unidentified senders. The security team is responding based on their incident response playbook. Which two elements are part of the eradication phase for this incident? (Choose two.)
A. anti-malware software
B. data and workload isolation
C. centralized user management
D. intrusion prevention system
E. enterprise block listing solution
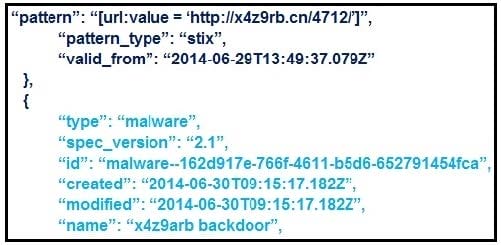
Refer to the exhibit. What is the IOC threat and URL in this STIX JSON snippet?
A. malware; `http://x4z9arb.cn/4712/'
B. malware; x4z9arb backdoor
C. x4z9arb backdoor; http://x4z9arb.cn/4712/
D. malware; malware--162d917e-766f-4611-b5d6-652791454fca
E. stix; `http://x4z9arb.cn/4712/'
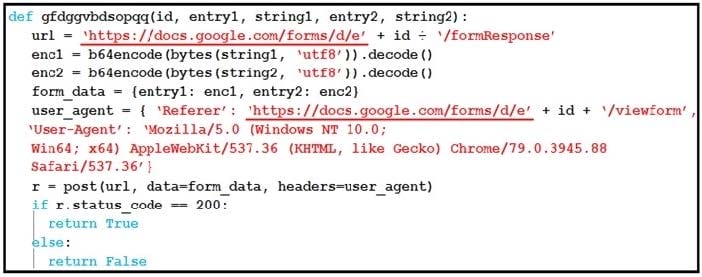
Refer to the exhibit. Which type of code is being used?
A. Shell
B. VBScript
C. BASH
D. Python
An "unknown error code" is appearing on an ESXi host during authentication. An engineer checks the authentication logs but is unable to identify the issue. Analysis of the vCenter agent logs shows no connectivity errors. What is the next log file the engineer should check to continue troubleshooting this error?
A. /var/log/syslog.log
B. /var/log/vmksummary.log
C. var/log/shell.log
D. var/log/general/log
Over the last year, an organization's HR department has accessed data from its legal department on the last day of each month to create a monthly activity report. An engineer is analyzing suspicious activity alerted by a threat intelligence platform that an authorized user in the HR department has accessed legal data daily for the last week. The engineer pulled the network data from the legal department's shared folders and discovered above average-size data dumps. Which threat actor is implied from these artifacts?
A. privilege escalation
B. internal user errors
C. malicious insider
D. external exfiltration

Refer to the exhibit. Which two actions should be taken based on the intelligence information? (Choose two.)
A. Block network access to all .shop domains
B. Add a SIEM rule to alert on connections to identified domains.
C. Use the DNS server to block hole all .shop requests.
D. Block network access to identified domains.
E. Route traffic from identified domains to block hole.
Which technique is used to evade detection from security products by executing arbitrary code in the address space of a separate live operation?
A. process injection
B. privilege escalation
C. GPO modification
D. token manipulation
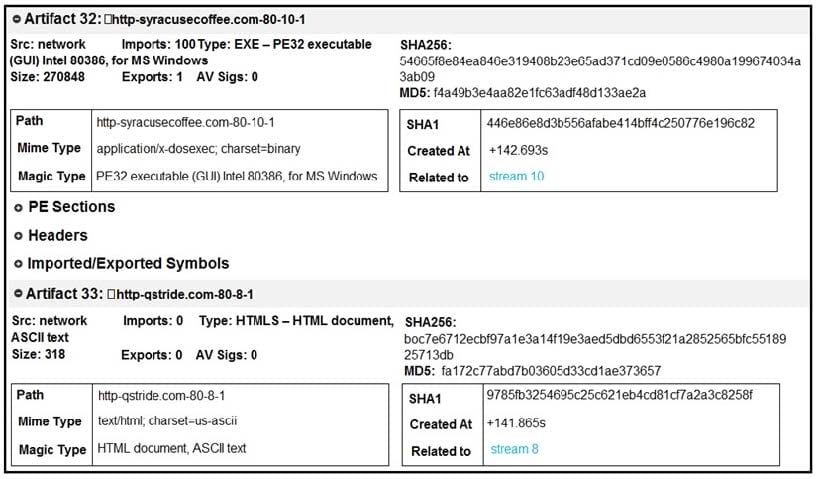
Refer to the exhibit. What do these artifacts indicate?
A. An executable file is requesting an application download.
B. A malicious file is redirecting users to different domains.
C. The MD5 of a file is identified as a virus and is being blocked.
D. A forged DNS request is forwarding users to malicious websites.
What are YARA rules based upon?
A. binary patterns
B. HTML code
C. network artifacts
D. IP addresses
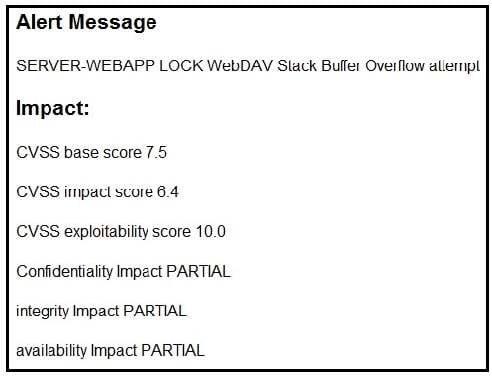
Refer to the exhibit. After a cyber attack, an engineer is analyzing an alert that was missed on the intrusion detection system. The attack exploited a vulnerability in a business critical, web-based application and violated its availability. Which two migration techniques should the engineer recommend? (Choose two.)
A. encapsulation
B. NOP sled technique
C. address space randomization
D. heap-based security
E. data execution prevention