250-438 Online Practice Questions and Answers
Which product is able to replace a confidential document residing on a file share with a marker file explaining why the document was removed?
A. Network Discover
B. Cloud Service for Email
C. Endpoint Prevent
D. Network Protect
Which channel does Endpoint Prevent protect using Device Control?
A. Bluetooth
B. USB storage
C. CD/DVD
D. Network card
A DLP administrator needs to stop the PacketCapture process on a detection server. Upon inspection of the Server Detail page, the administrator discovers that all processes are missing from the display. What are the processes missing from the Server Detail page display?
A. The Display Process Control setting on the Advanced Settings page is disabled.
B. The Advanced Process Control setting on the System Settings page is deselected.
C. The detection server Display Control Process option is disabled on the Server Detail page.
D. The detection server PacketCapture process is displayed on the Server Overview page.
Which two detection servers are available as virtual appliances? (Choose two.)
A. Network Monitor
B. Network Prevent for Web
C. Network Discover
D. Network Prevent for Email
E. Optical Character Recognition (OCR)
Refer to the exhibit.
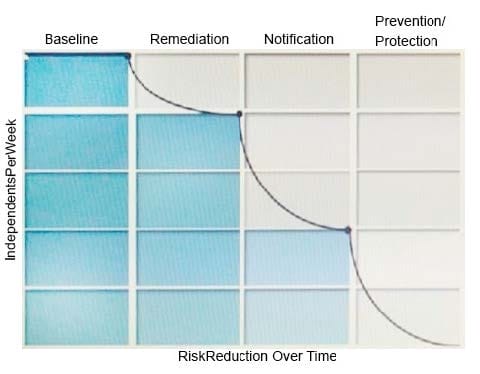
What activity should occur during the baseline phase, according to the risk reduction model?
A. Define and build the incident response team
B. Monitor incidents and tune the policy to reduce false positives
C. Establish business metrics and begin sending reports to business unit stakeholders
D. Test policies to ensure that blocking actions minimize business process disruptions
Which two DLP products support the new Optical Character Recognition (OCR) engine in Symantec DLP 15.0? (Choose two.)
A. Endpoint Prevent
B. Cloud Service for Email
C. Network Prevent for Email
D. Network Discover
E. Cloud Detection Service
A DLP administrator has performed a test deployment of the DLP 15.0 Endpoint agent and now wants to uninstall the agent. However, the administrator no longer remembers the uninstall password. What should the administrator do to work around the password problem?
A. Apply a new global agent uninstall password in the Enforce management console.
B. Manually delete all the Endpoint agent files from the test computer and install a new agent package.
C. Replace the PGPsdk.dll file on the agent's assigned Endpoint server with a copy from a different Endpoint server
D. Use the UninstallPwdGenerator to create an UninstallPasswordKey.
Where in the Enforce management console can a DLP administrator change the "UI.NO_SCAN.int" setting to disable the "Inspecting data" pop-up?
A. Advanced Server Settings from the Endpoint Server Configuration
B. Advanced Monitoring from the Agent Configuration
C. Advanced Agent Settings from the Agent Configuration
D. Application Monitoring from the Agent Configuration
