250-437 Online Practice Questions and Answers
Which detector will trigger if CloudSOC detects anomalously frequent sharing?
A. Behavior based
B. Threshold based
C. Sequence based
D. Threats based
Which CloudSOC module is similar to a Data Loss Prevention (DLP) system?
A. Detect
B. Investigate
C. Audit
D. Protect
Refer to the exhibit. Which module(s) use the CloudSOC gateway as a data source?
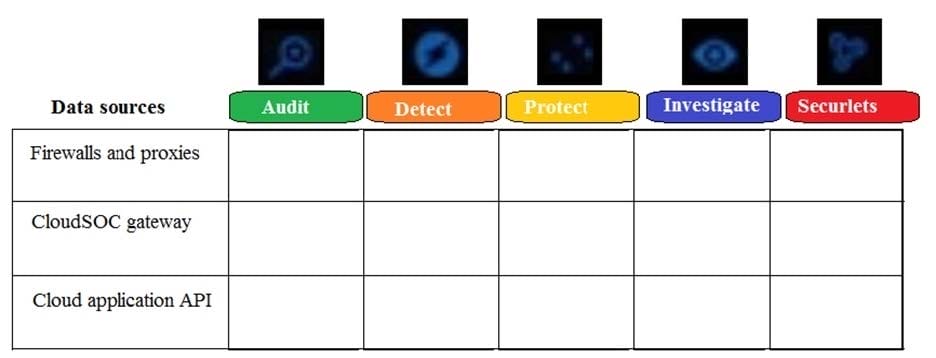
A. Audit
B. Detect and Protect
C. Detect, Protect, and Investigate
D. Detect, Protect, Investigate, and Securlets
What type of policy should an administrator utilize to prevent the spread of malware through cloud applications?
A. Access monitoring
B. File transfer
C. File sharing
D. Access enforcement
What policy should an administrator utilize to allow users access to Office 365, but prevent the extraction of files when their ThreatScore is higher than 30?
A. File transfer
B. Access enforcement
C. ThreatScore based
D. Data exposure
What Business Readiness Rating (BRR) category does the subcategory "Password Quality Rules" belong to?
A. Data
B. Compliance
C. Business
D. Access
How does the Securlet module get data?
A. Firewall and proxies
B. CloudSOC gateway
C. Cloud application APIs D. CloudSOC gateway and cloud application APIs
Refer to the exhibit. What modules are used by the use case "Identify and determine business risk of cloud applications being used within the organization"?
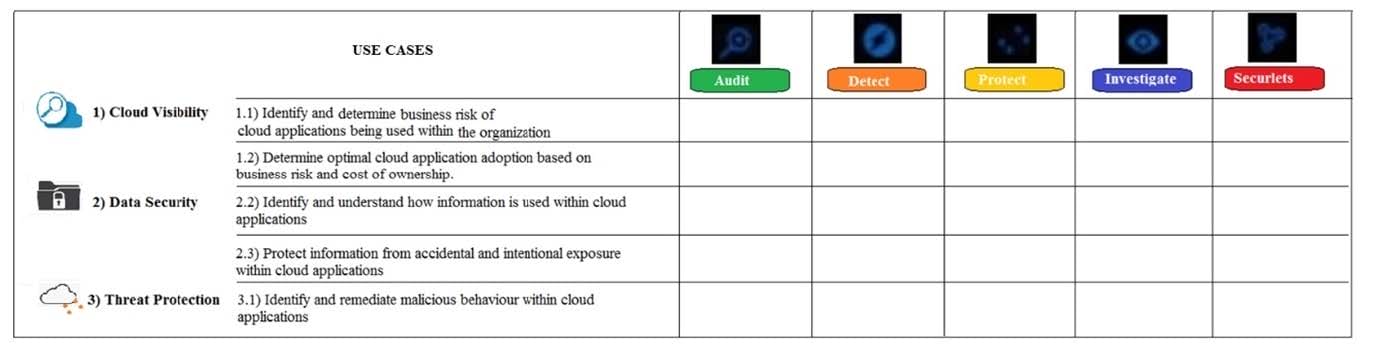
A. Investigate
B. Audit and Investigate
C. Audit
D. Audit and Securlets
Refer to the exhibit from the Investigate module. What type of policy should an administrator utilize to
prevent users from accessing files using an unmanaged device?
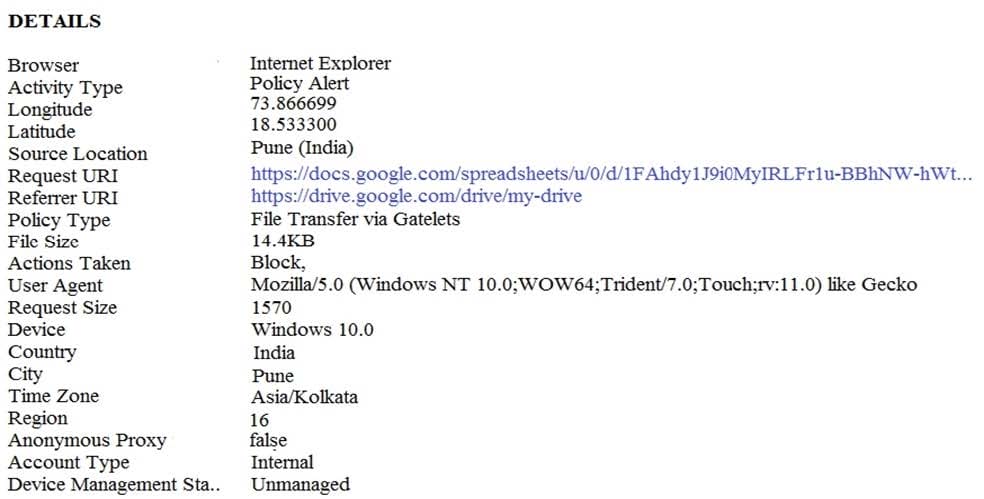
A. Access enforcement
B. File sharing
C. File transfer
D. Device enforcement
What Rule Type in ContentIQ profiles do FERPA, GLBA, HIPAA, PCI AND PII belong to?
A. Regular expressions
B. Content types
C. Risk types
D. Keywords
What type of connection should an administrator use when the network is sensitive to the bandwidth consumed by log traffic transfer to CloudSOC?
A. SCP
B. SpanVA
C. AWS S3 Bucket
D. APIs
What should an administrator use to identify document types specified by the user?
A. Custom dictionaries
B. Training profiles
C. Risk types
D. Content types
Who causes 80% of data leaks?
A. Hackers
B. Careless users
C. Malicious insiders
D. System administrators
What is the objective of the Access Monitoring policy?
A. To notify an administrator when activities, such as objects being modified, are performed in a cloud application.
B. To restrict the direct sharing of documents from cloud applications based both on their content and the characteristics of the user.
C. To prevent users from sharing documents, either publically, externally, or internally.
D. To restrict the uploading and downloading of documents from the user's computer to the cloud application, based both on the content of the documents and the characteristics of the user.
Where should an administrator locate the level of exposure in files in the Securlet module?
A. Exposure level
B. Exposed files
C. Exposed content
D. Exposure summary
