1D0-61C Online Practice Questions and Answers
A friend has called you about a possible computer problem because her computer is acting strangely. Sounds play unexpectedly, the monitor turns off suddenly, the hard-drive light flashes constantly, the computer sometimes reboots itself without warning. When you inspect your friend's system, you notice that several ports are open. Which of the following is most likely the cause of these symptoms?
A. The computer has been infected with a polymorphic virus.
B. The computer is experiencing a denial-of-service attack.
C. The computer has been infected with an illicit server.
D. The computer has been infected by a worm.
Which type of attack involves the installation of malicious code on personal computers or servers that redirects Internet traffic from a legitimate Web site to an identical-looking but malicious imposter Web site?
A. Pharming
B. Spoofing
C. Phishing
D. Replay
Which of the following computer system maintenance tasks can help improve file access performance?
A. Use a SCSI drive instead of a SATA drive
B. Use a SATA drive instead of an EIDE drive
C. Defragment the drive using the following command: fdisk -d -w c:/
D. Defragment the drive using the following command: defrag c: -w
Which of the following is a security threat commonly associated with cloud-based services?
A. Malware
B. Phishing
C. Hypervisor vulnerabilities
D. Operating system vulnerabilities
Gwen works for a small company where she has been asked to find a cost-effective option for providing comprehensive customer service. The finance, technical support, sales and customer service departments all need to share information about their customers. Gwen is considering adoption of a customer relationship management (CRM) application. Which of the following would be the most cost-effective solution?
A. She can purchase a new server, then create and maintain the CRM in-house.
B. She can outsource all customer service so the company can focus on product development.
C. She can contract with a cloud service provider to host the CRM that her company's employees can access.
D. She can hire a programmer to develop and maintain the CRM specific to her company's needs, then have a service provider host the application.
Selena has decided to change a 32-character unique wireless network name on her wireless router to improve network security after a break-in. She is following advice from CERT to make this change in order to avoid attacks from botnets. Which of the following settings would she modify?
A. Direct Sequence Spread Spectrum (DSSS) signal
B. Media Access Control (MAC) address
C. Wi-Fi Protected Access 2 (WPA2)
D. Service Set Identifier (SSID)
Henry is the network manager at XYY Corporation, a large manufacturing company that competes in the global market. The company's computing environment is extremely complex and includes several proprietary software systems, all of which require custom configuration of network devices to operate correctly. The company's executive management team believes that they can benefit by switching the company over to any cloud-based service. Henry disagrees.
What is a disadvantage of cloud-based services that Henry can cite to support his position?
A. Cloud-based services provide no maintenance or support.
B. Cloud-based services are typically more costly than in-house solutions.
C. The company must typically purchase additional servers to support connections to these types of cloud-based service providers.
D. Cloud-based services are typically more limited in offerings and configurations than the company currently supports in-house.
Disaster recovery planning is considered a best practice for all organizations. It is even more important when cloud-computing services are used. Which of the following should be included as part of a disaster recovery plan for companies that use cloud-based services?
A. Company organizational chart
B. Malware and anti-virus software updates
C. Service-level agreement with a cloud-provider
D. Inventory of services not dependent on the cloud provider
John is the network administrator for a small company. The company's network equipment has become outdated, and John has been asked to recommend a plan to update the company's infrastructure. John has read extensively about the many advantages of using cloud-based services. Which of the following is an advantage of cloud-based services that John could cite to support his recommendation?
A. Unlimited service options and choices
B. Higher security in a cloud-based environment
C. Elimination of need for high-speed Internet connection
D. Elimination of equipment purchase and maintenance
Mobile computing has become a common necessity for both personal and business transactions. Which device has features similar to a smartphone but usually does not have telephone capabilities?
A. Portable media player
B. Netbook
C. Laptop
D. Tablet
Consider the network configuration shown in the command prompt:
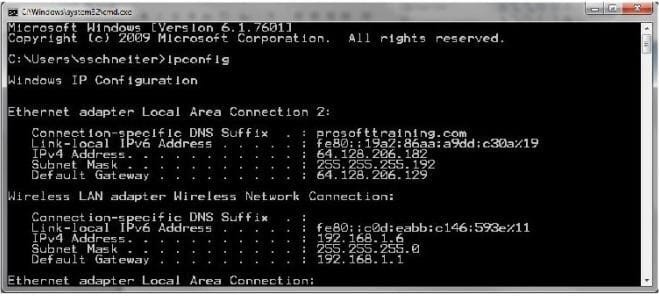
What does the Default Gateway identify?
A. The file server on the network
B. The local host on the network
C. The computer on the network
D. The router on the network
Ron has an older computer to which he frequently downloads and saves company files. He recently noticed that he was running low on disk space and decided to delete many old files that he no longer needed. He now notices that it takes a long time to open or save documents to his hard drive. Which maintenance task can help?
A. Disk defragmentation
B. chkdsk command
C. fdisk command
D. Disk cleanup
Carol is experiencing read/write errors when trying to save files on her Windows-based laptop. To correct the issue, she could consider performing which of the following maintenance tasks?
A. Disk cleanup
B. fsck command
C. chkdsk command
D. Disk defragmentation
Virtualization software transforms the hardware resources of a physical computer to create a fully functional virtual computer that can run its own operating systems and applications. In addition to the CPU and RAM, which hardware resources are used by virtualization software?
A. Hard disk and USB devices
B. Hard disk and network devices
C. Virtual hard disk and network devices
D. Network devices and secondary storage devices
Your company is investigating the possibility of moving its customer service management system to a cloud service provider. The sales rep for the cloud service provider has presented many advantages that would benefit your company. What would be a potential drawback of moving the CRM from your current in-house solution?
A. If your company's Internet service is interrupted for any reason at any time, you will not have access to the CRM.
B. More company employees will have access to the system, which could result in unauthorized access to confidential data
C. Special equipment will need to be purchased and maintained in your office in order to access and maintain the CRM once it is migrated to the hosted cloud service.
D. Migrating the CRM to the cloud service provider will eliminate several jobs in your customer service department because their job roles will no longer be required.
