156-215.81 Online Practice Questions and Answers
Check Point licenses come in two forms. What are those forms?
A. Security Gateway and Security Management.
B. On-premise and Public Cloud
C. Central and Local.
D. Access Control and Threat Prevention.
Fill in the blank Backup and restores can be accomplished through
A. SmartUpdate, SmartBackup. or SmartConsole
B. WebUI. CLI. or SmartUpdate
C. CLI. SmartUpdate, or SmartBackup
D. SmartConsole, WebUI. or CLI
What are the Threat Prevention software components available on the Check Point Security Gateway?
A. IPS, Threat Emulation and Threat Extraction
B. IPS, Anti-Bot, Anti-Virus, SandBlast and Macro Extraction
C. IPS, Anti-Bot, Anti-Virus, Threat Emulation and Threat Extraction
D. IDS, Forensics, Anti-Virus, Sandboxing
What is the default tracking option of a rule?
A. Tracking
B. Log
C. None
D. Alert
The SIC Status "Unknown" means
A. There is connection between the gateway and Security Management Server but it is not trusted.
B. The secure communication is established.
C. There is no connection between the gateway and Security Management Server.
D. The Security Management Server can contact the gateway, but cannot establish SIC.
Which Threat Prevention Software Blade provides protection from malicious software that can infect your network computers? (Choose the best answer.)
A. IPS
B. Anti-Virus
C. Anti-Malware
D. Content Awareness
What are the three main components of Check Point security management architecture?
A. SmartConsole, Security Management, and Security Gateway
B. Smart Console, Standalone, and Security Management
C. SmartConsole, Security policy, and Logs and Monitoring
D. GUI-Client, Security Management, and Security Gateway
Using R80 Smart Console, what does a "pencil icon" in a rule mean?
A. I have changed this rule
B. Someone else has changed this rule
C. This rule is managed by check point's SOC
D. This rule can't be changed as it's an implied rule
Which two Identity Awareness daemons are used to support identity sharing?
A. Policy Activation Point (PAP) and Policy Decision Point (PDP)
B. Policy Manipulation Point (PMP) and Policy Activation Point (PAP)
C. Policy Enforcement Point (PEP) and Policy Manipulation Point (PMP)
D. Policy Decision Point (PDP) and Policy Enforcement Point (PEP)
Which two of these Check Point Protocols are used by ?
A. ELA and CPD
B. FWD and LEA
C. FWD and CPLOG
D. ELA and CPLOG
Fill in the blank: An Endpoint identity agent uses a ___________ for user authentication.
A. Shared secret
B. Token
C. Username/password or Kerberos Ticket
D. Certificate
Which statement is TRUE of anti-spoofing?
A. Anti-spoofing is not needed when IPS software blade is enabled
B. It is more secure to create anti-spoofing groups manually
C. It is BEST Practice to have anti-spoofing groups in sync with the routing table
D. With dynamic routing enabled, anti-spoofing groups are updated automatically whenever there is a routing change
You noticed that CPU cores on the Security Gateway are usually 100% utilized and many packets were dropped. You don't have a budget to perform a hardware upgrade at this time. To optimize drops you decide to use Priority Queues and fully enable Dynamic Dispatcher. How can you enable them?
A. fw ctl multik dynamic_dispatching on
B. fw ctl multik dynamic_dispatching set_mode 9
C. fw ctl multik set_mode 9
D. fw ctl miltik pq enable
Which is a suitable command to check whether Drop Templates are activated or not?
A. fw ctl get int activate_drop_templates
B. fwaccel stat
C. fwaccel stats
D. fw ctl templates -d
Administrator Dave logs into R80 Management Server to review and makes some rule changes. He notices that there is a padlock sign next to the DNS rule in the Rule Base.
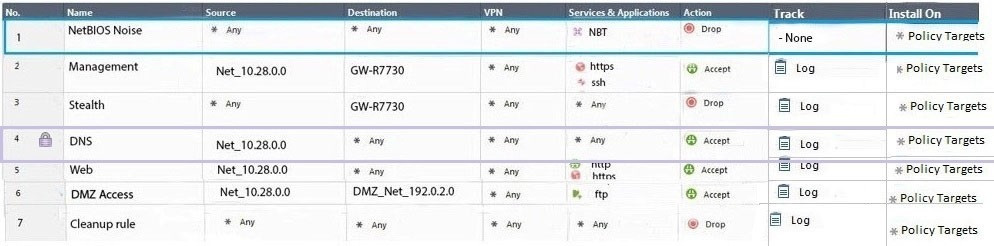
What is the possible explanation for this?
A. DNS Rule is using one of the new feature of R80 where an administrator can mark a rule with the padlock icon to let other administrators know it is important.
B. Another administrator is logged into the Management and currently editing the DNS Rule.
C. DNS Rule is a placeholder rule for a rule that existed in the past but was deleted.
D. This is normal behavior in R80 when there are duplicate rules in the Rule Base.
