210-255 Online Practice Questions and Answers
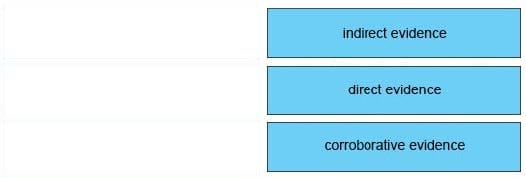
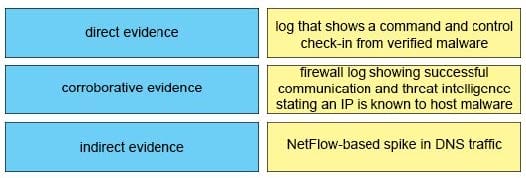
Drag and drop the type of evidence from the left onto the correct descnption(s) of that evidence on the right.
Select and Place:
DRAG DROP
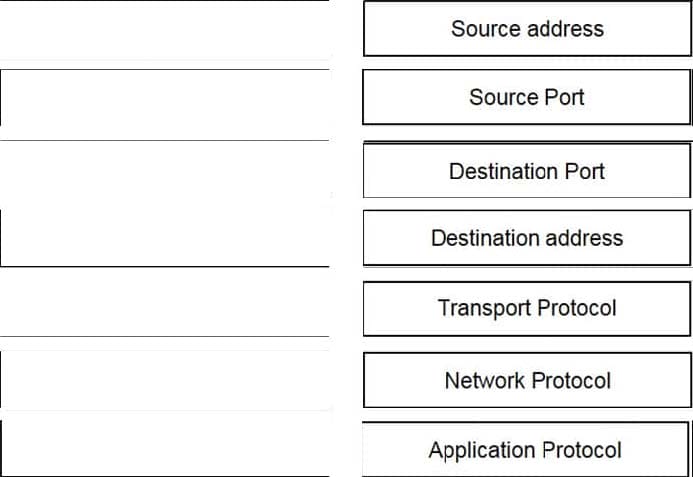
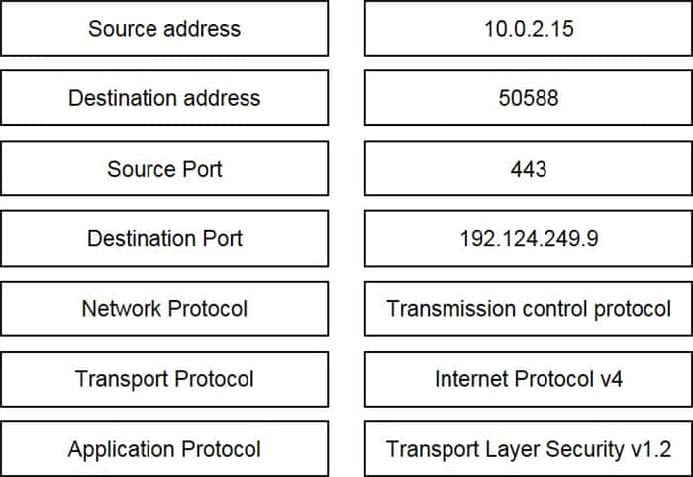
Refer to the exhibit. Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
Select and Place:
You see 100 HTTP GET and POST requests for various pages on one of your webservers. The user agent in the requests contain php code that, if executed, creates and writes to a new php file on the webserver. Which category does this event fall under as defined in the Diamond Model of Intrusion?
A. delivery
B. reconnaissance
C. action on objectives
D. installation
E. exploitation
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
A. collection
B. examination
C. reporting
D. investigation
A CMS plugin creates two files that are accessible from the Internet myplugin.html and exploitable.php. A newly discovered exploit takes advantage of an injection vulnerability in exploitable.php. To exploit the vulnerability, one must send an HTTP POST with specific variables to exploitable.php. You see traffic to your webserver that consists of only HTTP GET requests to myplugin.html. Which category best describes this activity?
A. weaponization
B. exploitation
C. installation
D. reconnaissance
Which option is a misuse variety per VERIS enumerations?
A. snooping
B. hacking
C. theft
D. assault
Which of the following is one of the main goals of data normalization?
A. To save duplicate logs for redundancy
B. To purge redundant data while maintaining data integrity
C. To correlate IPS and IDS logs with DNS
D. To correlate IPS/IDS logs with firewall logs
Which of the following is not an example of weaponization?
A. Connecting to a command and control server
B. Wrapping software with a RAT
C. Creating a backdoor in an application
D. Developing an automated script to inject commands on a USB device
Which of the following are the three broad categories of cybersecurity investigations?
A. Public, private, and individual investigations
B. Judiciary, private, and individual investigations
C. Public, private, and corporate investigations
D. Government, corporate, and private investigations
What attribute belonging VERIS schema?
A. confidentiality/possession
B. integrity/authenticity
C. availability/utility
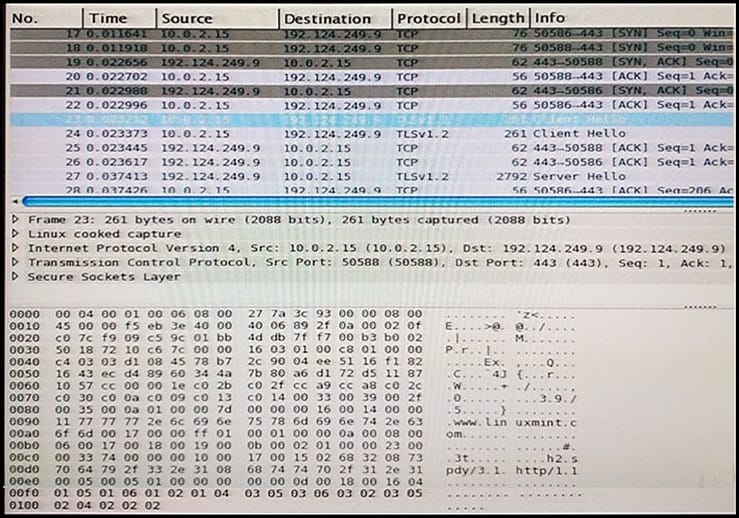
Refer to exhibit. Which option is the logical source device for these events?
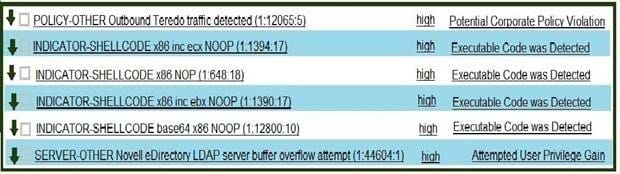
A. web server
B. NetFlow collector
C. proxy server
D. IDS/IPS
Which purpose of data mapping is true?
A. Visualize data.
B. Find extra vulnerabilities.
C. Discover the identities of attackers
D. Check that data is correct.
What is a job in Microsoft Windows?
A. A job is a group of threads.
B. A job is a group of hives.
C. A job is a group of services.
D. A job is a group of processes.
What do the Security Intelligence Events within the FMC allow an administrator to do?
A. See if a host is connecting to a known-bad domain.
B. Check for host-to-server traffic within your network.
C. View any malicious files that a host has downloaded.
D. Verify host-to-host traffic within your network.
Refer to the exhibit.
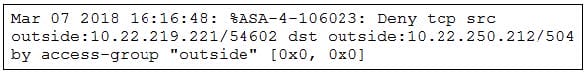
Which technology generates this log?
A. NetFlow
B. IDS
C. web proxy
D. firewall