210-250 Online Practice Questions and Answers
Which access control model uses the function of a subject in an organization?
A. Discretionary access control
B. Attribute-based access control
C. Role-based access control
D. Mandatory access control
Which AAA protocol allows for capabilities exchange?
A. RADIUS
B. TACACS+
C. Diameter
D. Kerberos
In which enterprise patch management model can the system can install a patch automatically?
A. Agentless
B. Passive
C. Agent based
D. Install based
Which of the following statements is true about clientless SSL VPN?
A. The client must use a digital certificate to authenticate.
B. The remote client needs only an SSL-enabled web browser to access resources on the private network of the security appliances.
C. Clientless SSL VPNs do not provide the same level of encryption as client based SSL VPNs.
D. Clientless SSL VPN sessions expire every hour.
Which tool provides universal query access to text-based data such as event logs and file system?
A. log parser
B. Windows Management Instrumentation
C. handles
D. service viewer
Which option is true when using the traffic mirror feature in a switch?
A. Packets are automatically decrypted.
B. Ethernet headers are modified before capture.
C. Packet payloads are lost.
D. Full packet captures are possible.
A system administrator installs an IDS to protect users on 10.2.3.0/24. After the installation, users can see only other machines on their /24 consistently and cannot reach external sites. Which possible explanation is true?
A. The IDS is working properly and providing the users on 10.2.3.0/24 with the security they need
B. The IDS was configured to fail open and has not yet been fully configured
C. The IDS was installed inline and is dropping traffic that must be allowed
D. The system administrator mirrored the traffic for that network segment and did not tune the IDS properly
In Windows Operating System, an application cannot directly access an object data or system resource that an object represents. Which option must the application obtain to examine the object data or system resource?
A. registry
B. ACLs
C. handles
D. WMI
Why would an attacker use Mimikatz once they gained access to a system?
A. to create a tunnel for covert communication channels back to the attacker network
B. to list the user accounts currently logged on to the machine
C. to create a new domain user account to log in to so regular users will not notice their activity
D. to extract passwords and hashes for user accounts that have logged on to the system
Which two statements are true about password hashing? (Choose two.)
A. Hashing produces a fixed-length "fingerprint" of the data that cannot be reversed.
B. Password hashing is becoming less effective as attackers become increasingly proficient at salting.
C. Hashing hides the true password value when passed over the network.
D. Some protocols or applications do not support hashing.
Which two best describe iFrames? (Choose two.)
A. a new Apple product
B. hidden inline frames
C. loading a webpage inside another webpage
D. a frame within a browser where a user can view the page's source code
What are two examples of common database platforms that are used on Linux devices? (Choose two.)
A. MySQL
B. WinSQL
C. SQL-lite
D. NoSQL
What does the chmod 766 command do to a file?
A. changes the file's read/write/execute permissions to a desired configuration B. changes the filename from 766 to whatever value is set in the section
C. It does nothing; it is an illegal command.
D. deletes the file that is identified in the description
To provide origin authentication, the sender encrypts the message using an asymmetric encryption algorithm. In this case, the receiver of the message must use what to decrypt the message?
A. sender's digital signature
B. sender's shared key
C. sender's private key
D. sender's public key
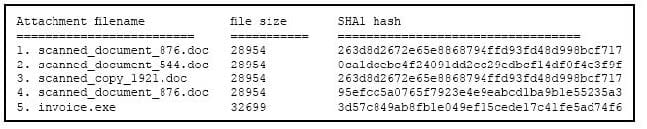
Refer to the exhibit. During an analysis, this list of email attachments is found. Which files contain the same content?
A. 1 and 4
B. 3 and 4
C. 1 and 3
D. 1 and 2
