1D0-571 Online Practice Questions and Answers
A distributed denial-of-service (DDOS) attack has occurred where both ICMP and TCP packets have crashed the company's Web server. Which of the following techniques will best help reduce the severity of this attack?
A. Filtering traffic at the firewall
B. Changing your ISP
C. Installing Apache Server rather than Microsoft IIS
D. Placing the database and the Web server on separate systems
Which of the following organizations provides regular updates concerning security breaches and issues?
A. IETF
B. ISO
C. ICANN
D. CERT
The most popular types of proxy-oriented firewalls operate at which layer of the OSI/RM?
A. Application layer B. Network layer
C. Session layer
D. Transport layer
The best way to thwart a dictionary attack is by enforcing a:
A. strong password policy.
B. restricted access policy.
C. firewall configuration policy.
D. proxy server policy.
Which algorithm can use a 128-bit key, and has been adopted as a standard by various governments and corporations?
A. MARS
B. RC2
C. Advanced Encryption Standard (AES)
D. International Data Encryption Algorithm (IDEA)
Which tool is best suited for identifying applications and code on a Web server that can lead to a SQL injection attack?
A. A vulnerability scanner
B. A packet sniffer
C. An intrusion-detection system
D. A network switch
Which of the following applications can help determine whether a denial-of-service attack is occurring against a network host?
A. Thenetstat command and a packet sniffer
B. Theps command and a network scanner
C. The ping command and User Manager
D. Theiptables command and Windows desktop firewall
Consider the following diagram:
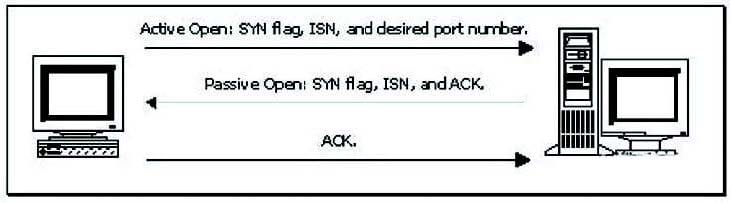
Which of the following best describes the protocol activity shown in the diagram, along with the most likely potential threat that accompanies this protocol?
A. The ICMP Time Exceeded message, with the threat of a denial-of-service attack
B. The SIP three-way handshake, with the threat of a buffer overflow
C. The TCP three-way handshake, with the threat of a man-in-the-middle attack
D. The DNS name query, with the threat of cache poisoning
